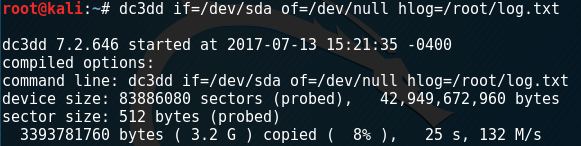
Typical terminal output when imaging a drive using Linux Application dc3d
Used for many functions, including data recovery and digital forensics, image copies and files copies each have their own specific purposes. In some cases, using the wrong type of copy can have consequences from wasting some extra time to corrupting digital evidence. Let’s compare the differences between an image copy and a file copy and give some examples of when each is best used.
Explaining an Image Copy and its Uses in Data Recovery and Digital Forensics
An image copy is the precise clone of a drive, sector-by-sector, all the ones and zeroes included. When a drive is backed up this way, the absolute exact state of the drive at that time is saved for future reference. When a file is stored on a drive, it doesn’t always overwrite every byte of the file previously stored in the same spot, and extra data from the old file may still exist on the drive. An image copy will preserve this extra data whereas a file copy will ignore it.
For digital forensics, extra data existing on a drive can be a treasure-trove of clues and evidence. Forensic analysts must create image copies of suspect drives to enable a complete analysis. Any tests on the data should be done on the image copy instead of the original drive, keeping it safe from unintentional contamination. Examining a piece of evidence before imaging it, is something to be avoided. An image copy may also need to be given to a legal opponent to examine the drive on their own, in its entirety. By handing over an image copy, the opponent can’t possibly harm the original source drive in evidence.


 Hard Drive Storage Capacity Calculations
Hard Drive Storage Capacity Calculations



